Free Cyber Security Risk Assessment
Are you not sure where to start in your organisations cyber security risk assessment? Cybersecurity Risk Assessment is not just a buzzword; it’s the cornerstone of safeguarding digital fortresses against threats lurking in the shadows. That’s where frameworks like the CIS (Center for Internet Security) come into play, offering a structured approach to evaluate and mitigate cyber risks.
This Free Cybersecurity Risk Assessment is a process I use for many business regardless of their size, utilising the Centre of Internet Security (CIS) open source documents, available to everyone online. This article will demonstrate nuances and how to complete one of these assessments. This isn’t a “fill out a form and get a result” type scenario, you are responsible for the upkeep and ongoing health of the assessment.
Get your copy of the CIS Controls
Outcome
The outcome of the CIS Risk Assessment will include:
- Identification and prioritisation of risks based on their likelihood and potential impact, enabling focused and effective risk mitigation efforts.
- Wholistic risk outline per CIS Control allowing you to develop long-term strategic plans
- A methodology that enables Cyber Security / I.T Engineers without guess-work
- Provision of actionable insights to executive leadership and IT management, facilitating informed decision-making regarding cybersecurity investments and priorities.
- Enhanced ability to make risk-based decisions that balance security needs with business objectives.
Included in this process is a spreadsheet that highlights each CIS control and its level of risk:
This allows I.T and Cyber staff to easily understand where the shortcomings of their cybersecurity controls that are currently in place and which controls are more important to implement.
Why Choose the CIS Framework?
The CIS Framework is a great building block for organisations to harness to perform a cybersecurity risk assessment due to its simplicity and free online tools available to the public. During the course of this article you will also be utilising these free online tools to protect information systems, implementing information security.
The NIST framework is complicated, has hundreds of sub controls and can be extremely overwhelming. While CIS does have some controls I wish were stronger, it’s going to do the job for organisations of any size. CIS when approaching RISK particularly does not use a quantitative approach to risk, the means you are not calculating the likelihood of a single laptop in the organisation getting infected. Rather we are trying to understand contextually what is important to your organisation and what IMPACT a cyber event could cause.
Free Cyber Security Risk Assessment Methodology?
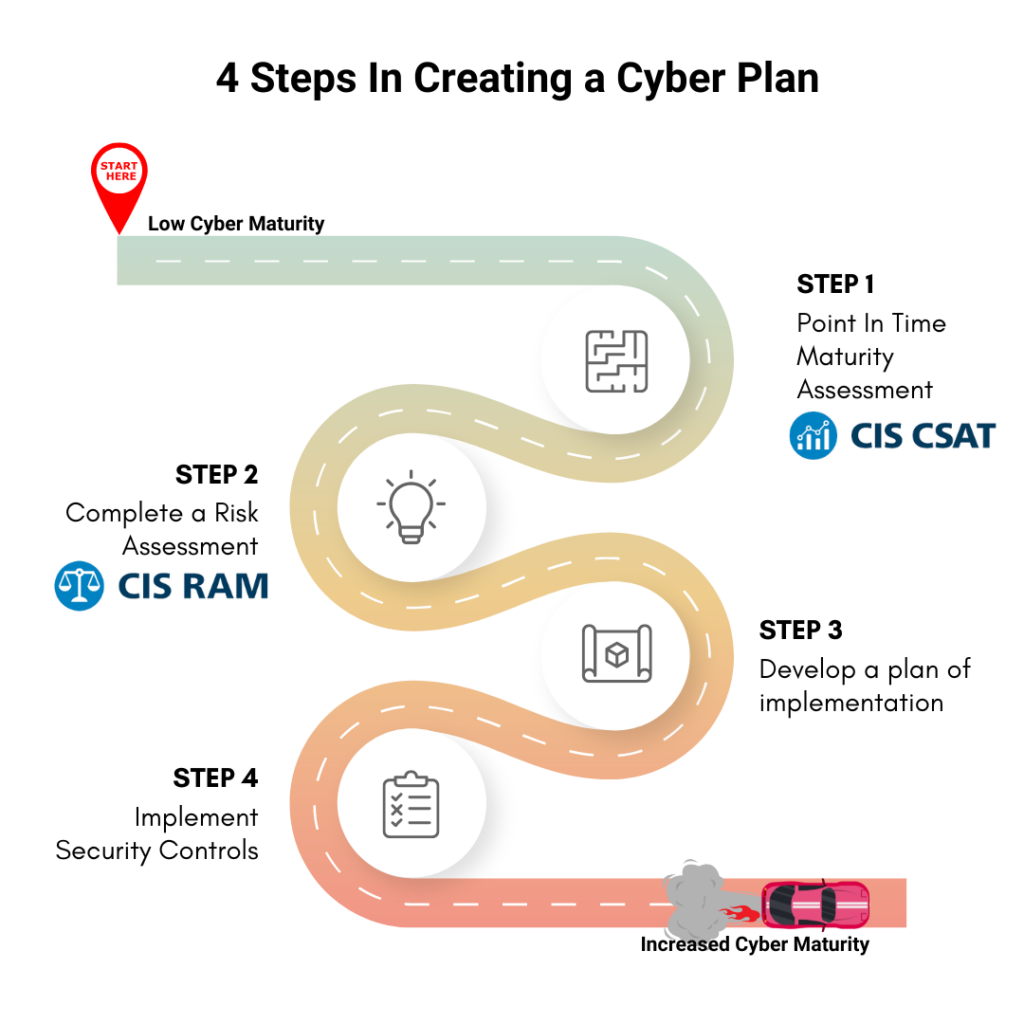
This methodology follows the below steps:
- Step 1: Point in time Maturity Assessment
- An assessment to understand what level of protection you have in each cyber security control. This ranges from Endpoint Security to Email.
- Step 2: Completing a Risk Assessment
- Utilise the information collected in the Point In Time assessment and begin building out information about your organisation.
- Step 3: Develop a plan of implementation
- Create a Cyber Security Plan of focus to implement controls
- Step 4: Implement Security Controls
- When you understand your maturity and risks, you overcome these controls with technical implementations to ensure you are increasing your cyber security maturity
The CIS Controls
The CIS Controls Version 8, developed by the Center for Internet Security (CIS), are a set of prioritised actions designed to mitigate the most common cyber threats and vulnerabilities. These controls are organized into three implementation groups based on their relevance to various organisations: Basic (First 6 Controls), Foundational(Control 7-12), and Organisational (Control 13-18).
The CIS framework emphasises the importance of a proactive and adaptable cybersecurity strategy by integrating concepts such as resilience, automation, and continuous improvement. It places a greater emphasis on foundational cybersecurity principles like asset management, vulnerability management, and identity and access management, which are essential components of any robust security posture. By implementing the CIS Controls Version 8, organisations can strengthen their cybersecurity resilience and better protect themselves against a wide range of cyber threats, ultimately enhancing their overall security posture.
CIS Implementation Groups
Anything referenced in these guides will be based on the CIS Framework Implementation Group (IG) 2. This is similar to the Essential 8 Maturity levels if you are familiar. Depending on the maturity of the organisation you can implement more controls to ensure you are compliant. Choosing a higher level IG means more work… but increases the control level.
With a total of 153 safeguards throughout the CIS framework, you will be working to implement all of them in this process and effectively reduce the risk that your organisation may current have.
Step 1: Point in time Maturity Assessment
A point in time maturity assessment is a reflection of how many controls your organisation has currently implemented. It is expected that the results in your first assessment… are quite low. This means there are some quick wins to increase your maturity across the organisation and begin to boost the current level of maturity.
How do you measure your level of maturity?
CIS offer a free tool call CIS Self Assessment Tool (CSAT), designed to choose your IG maturity level and step you through each sub control and answer important questions. These questions include:
- Have you implemented a policy?
- Have you implemented the control?
- Have you automated the control?
- Do you report on the control?
Answering these questions derives a score for each control that is used to create the graphs within the interface and an overall score.
Your score is measured in many different types of graphs within the CSAT portal where it outlines your maturity for every control. Each control has a different total of sub controls which means the maturity is measured from 0-100 on a scale.
Step 2: Complete a risk assessment
CIS offers another free tool called the Risk Assessment Methodology (RAM) that is kept within a spreadsheet that calculates your risks. As mentioned above, a point in time score does not equal a level of risk so ensuring the risk assessment process is followed to reach a conclusion of risk is important.
To summarise this process:
- Create impact statements for your organisation.
- Define Enterprise Parameters for your organisation
- Import your CIS CSAT results into the platform
Impact Criteria
The impact criteria is designed for you to fully understand your organisation from a “business” perspective rather than an IT perspective. At the end of the Risk Assessment, it should be easy to understand the translate your cyber risk to “business speak” thanks to completing these components.
Impact statements are based on 4 categories:
- Mission Objectives
- Operational Objectives
- Financial Objectives
- Obligations
These items are typically already known by parts of the business other than the I.T or cyber department. It’s important to speak to other parts of the organisation that know more about these topics; HR, finance, CEO, COO and others.
Once you have defined these items, they need to be met with “impact responses” for the following categories:
- Negligible
- Acceptable
- Unacceptable
- High
- Catastrophic
Once this is complete you will end up with something similar to this:
Mission: Reliably produce just-in-time, custom widgets that meet demanding resiliency and design specifications, and within market-leading turnaround times.
Negligible: All orders would be produced within specifications and on time and without unplanned effort.
Acceptable: All orders would be produced within specifications and on time, but some may require unplanned effort to stay within tolerance metrics.
Unacceptable: Few orders each quarter (outside of our tolerance metrics) may miss targets, but could be corrected with adjustments or discounts.
High: We would repeatedly miss targets outside of tolerance metrics, requiring regular adjustments or discounts per quarter, or would require significant re-investment to operate regularly within our tolerance metrics.
Catastrophic: We could not meet our mission.
Risk Acceptance Criteria
Each organisation accepts a certain level of risk and defining exactly what the means is important. To do this we simply use two different tables of information:
Expectancy Criteria:
A 1-5 score that determines your expectation or “likeliness” that you expect that something would happen
| Expectancy Score | Expectancy | Criteria |
| 1 | Remote | Safeguard would reliably prevent the threat. |
| 2 | Unlikely | Safeguard would reliably prevent most occurrences of the threat. |
| 3 | As likely as not | Safeguard would prevent as many threat occurrences as it would miss. |
| 4 | Likely | Safeguard would prevent few threat occurrences. |
| 5 | Certain | Safeguard would not prevent threat occurrences. |
A 1-5 core of how much impact a cyber attack event would have on the business
Impact Scores:
| Impact Scores |
| Definition |
| 1. Negligible |
| 2. Acceptable |
| 3. Unacceptable |
| 4. High |
| 5. Catastrophic |
These scores are multiplied and creates a base level of “risk acceptance” within the organisation. At the end of the results anything with a lower score than these two numbers multiplied will be considered a “risk”.
Risk Criteria Results
| Expectancy | Impact |
| 3 | 3 |
| Acceptable Risk is less than … | 9 |
In this case, your acceptable risk is less than 9.
Inherent Risk Criteria
We’ve spoken about business definitions and risk… but we know all of these terms are related directly to what we want to protect; assets and information. This component is geared for you to rate your assets based on how much impact they would have on your business definitions (mission objectives, obligations) using the impact scores above. For example, you may be most concerned about Data which would impact all of your impact statements catastrophically, hence you would score these as a 5. If your organisation primarily uses SaaS applications, impact on your ‘network’ probably wont be a problem for the business and can be scored lower.
Here is an example of the Inherent Risk Criteria.
Import your CSAT Results
The CSAT results indicate the level of maturity in each control. You can download the CSAT results from the portal, once you have completed the CIS CSAT. These results can be copy and pasted into the RAM spreadsheet as a baseline of maturity.
The CSAT results are cross referenced throughout the CIS V8 cyber security framework to determine the risk level of each sub control, resulting in a level of risk.
CIS RAM CyberSecurity Risk Assessment Results
The CIS RAM results can now be found throughout the spreadsheet, where the cross referenced results for the previous information about the business with the CIS CSAT scores to determine what can be effected. Each control within the CIS framework is traffic lit green, yellow or red to determine what the risk is. Focusing on the red controls is the most important from a risk perspective.
Congratulations! You now have your first risk assessment complete now. Developing a plan for remediation and implementation by developing a cybersecurity program to protect each information system within your network and cloud environments is important. If you need help with this, feel free to reach out to [email protected] and we can develop the next steps.
This series is intended to be an overview of the CIS RAM process rather than a walkthrough. In future, a walkthrough can be provided that breaks down these steps in further details.
