The CIS Self Assessment Tool (CIS CSAT) is a tool that Cyber Security experts and I.T analysts use to understand the strength of a CIS control implementation. The stronger the control, the less likely a cyber attack is to occur. The CSAT is a Point-In-Time assessment which can be referenced in future to understand the growth of an organisations cyber security posture and is completed across all CIS controls. Importantly, the CSAT is a key component and prerequisite of the next stage in a risk assessment, the CIS RAM.
Follow this tutorial to fully understand how to complete a CIS Self Assessment.
Sign Up For CSAT
CIS provides a free online tool to complete the CSAT. Sign up for a CIS CSAT account via the following link:
https://csat.cisecurity.org/accounts/login/?next=
To sign up, you cannot use a freemail email address only a custom purchased domain. During the sign up stage you are also asked what industry the organisation works in which can be changed in the future, but is important as the average CIS Control Scores of that industry will be shown in the CSAT portal.
CIS Control Refresher
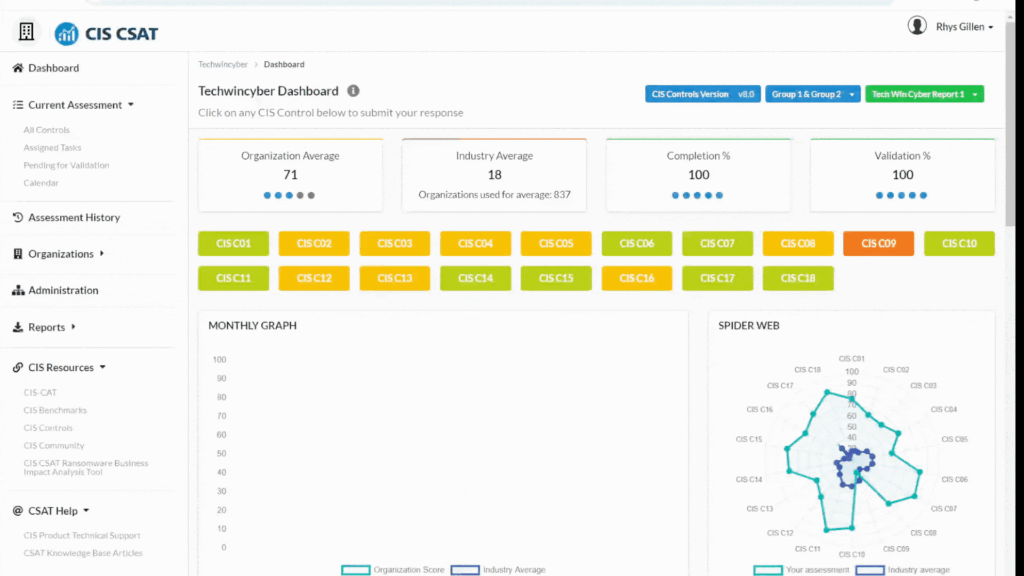
Total Number of Controls
The Center for Internet Security (CIS) Controls are a set of best practices aimed at helping organisations enhance their cybersecurity posture. Initially developed by a global community of experts, these controls provide a concise, prioritised list of actions to mitigate the most prevalent cyber threats.
The CIS Controls are structured into 18 distinct categories, each addressing a specific area of cybersecurity, from inventory and control of hardware and software assets to incident response and management. The framework is designed to be comprehensive yet flexible, enabling organisations of varying sizes and industries to implement these practices effectively. It follows a tiered approach, making it easier to adopt and scale according to an organisation’s maturity level.
Get your copy of the CIS Controls
Implementation Groups
Each of the 18 CIS controls will need to be answered to complete this assessment and each control contains subcontrols. The CIS Controls are divided into Implementation Groups (IGs), with IG1 focusing on basic cyber hygiene essential for all organisations, IG2 addressing more complex controls for organisations handling sensitive information, and IG3 targeting advanced security measures for high-risk environments. In this tutorial, we will be completing Implementation Group (IG) 2 which has 74 sub controls.
Getting Started GIF
The sub controls all have definitions, we can see the first Control: Inventory and Control of Enterprise Assets has four controls within Implementation Group 2:
1.1 Establish and Maintain Detailed Enterprise Asset Inventory
1.2 Address Unauthorized Assets
1.3 Utilize an Active Discovery Tool
1.4 Use Dynamic Host Configuration Protocol (DHCP) Logging to Update Enterprise Asset Inventory
In the next steps, you will be reviewing all sub controls for all 18 CIS controls. Let’s start with Control 1.1 – Establish and Maintain Detailed Enterprise Asset Inventory which is defined at the stop of the page:
To measure this sub control you will be asked to complete 4 items of information:
- Policy Defined
- Control Implemented
- Control Automated
- Control Reported
These definitions are outlined in the CIS product knowledge guide as:
Policy Defined
- To what degree is this Sub-Control covered by your organization’s policies?
Control Implemented
- To what degree has your organization implemented this Sub-Control?
- This can factor in coverage (such as what percentage of the machines in your organization have this Sub-Control implemented) and/or level of implementation (for instance, all machines in your organization could have the Sub-Control partially implemented).
Control Automated
- To what degree does your organization enforce this Sub-Control through automated means vs. manual/procedural means?
Control Reported
- To what degree is the state of this Sub-Control being reported within your organization, generally to leadership or management?
- Are updates on the state of that Sub-Control’s implementation getting to where they need to go (to the decision makers who can act on them, to those who can decide if the organization needs to invest more to improve that Sub-Control’s implementation in order to reduce risk, to meet any reporting requirements the organization has including requirements from organizational policies or from regulatory requirements, etc.)?
Each answer will contribute to the total maturity level of the control. For example if you selected:
In this example, the score for this sub control will be extremely mature. If you have none of the above completed, your score will be lower. Remember the reason we are completing the CSAT is to use these results in the CIS Risk Assessment Methodology (RAM). Having low scores at the end of the CIS CSAT will enable the CIS RAM to quickly identify what controls need to be increased.
Ensure that each sub control is given enough attention and that the answers are correct. This can be helped by uploading direct evidence in the portal such as the written policy. Due to the CIS Controls being varied across many disciplines you may want to invite other experts of their domains to the CSAT portal and assign the ability for them to fill out the results.
Speed Running the CSAT
When updating the CIS for the second time you may only need to focus on updating specific sub controls. There is a faster way to view all sub control inputs by selecting the All Controls:
Here you can see all of the sub controls and their status, quickly being able to use the drop down boxes to select any changes to the controls.
Exporting the CSAT Results
Exporting the results from the CSAT portal is easy. Use the left hand menu and select All Controls and use the Download Report button. This will download an excel spreadsheet with your CSAT results and can be used in the RAM.
Reporting
There are three executive reports that come from the CSAT; Board level slides, Control Summary Reports, Control Status Report (CSR). The reports are reasonably basic and need to be pulled re-worked when they are presented to the business.
Example Default Executive slide:
This is a complete overview of utilising the CSAT to complete a benchmark against your organisation. This information is extremely important to understand the maturity of your environment against the CIS framework.
Again – a weak control does not mean you need to focus on increasing its maturity as a priority. The priority should be based on the risk of the organisation. For example, if you don’t create applications in-house then focusing on a weak Control 16: Application Software Security as it defines application security.
